Proxy Service POP3/IMAP Authentication Integration
Summary
IMAP allows you to access your e-mail from anywhere and from any device. When you read your e-mail using IMAP, you won’T actually download or store the e-mail on your computer; you be reading it from the e-mail service.
As a result, you can check your e-mail from different devices around the world, such as your phone, your computer, or your friend’s computer. IMAP downloads the message you clicked and attachments are not downloaded automatically.
Pop works by contacting your email service and downloading all your new e-mail from there. After they are these downloaded to your computer, they are deleted from the e-mail service. After downloading the e-mail can only be accessed using the same computer. If you try to access your e-mail from a different device, you will not receive email that have been downloaded before. Sent mail is stored locally on your computer, not on the e-mail server.
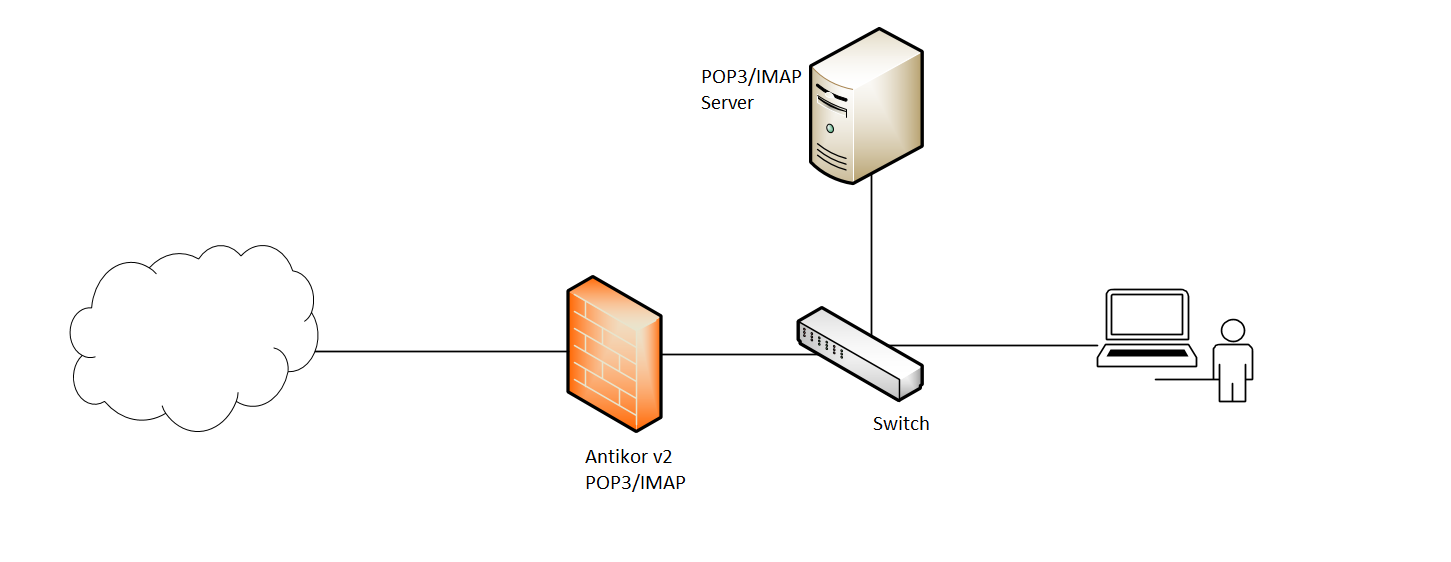
Network Topology
Configuration
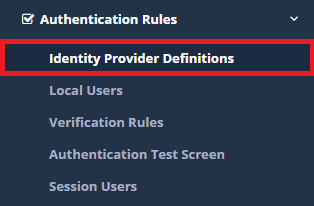
1) Firstly, click the Identity Provider Definitions under the Authentication Rules menu.
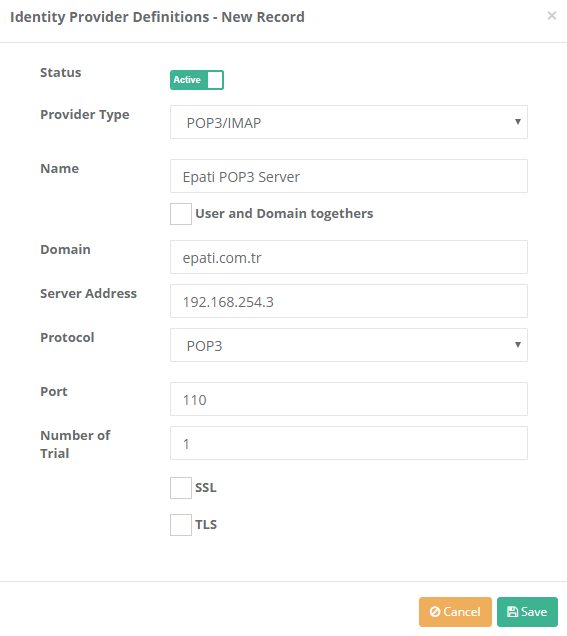
2) Click the Add button to enter he required information about the POP3 / IMAP server.
3) Click the Verification Rules under the Authentication Rules menu. Then are go to the proxy tab and the following are operations are performed in sequence.
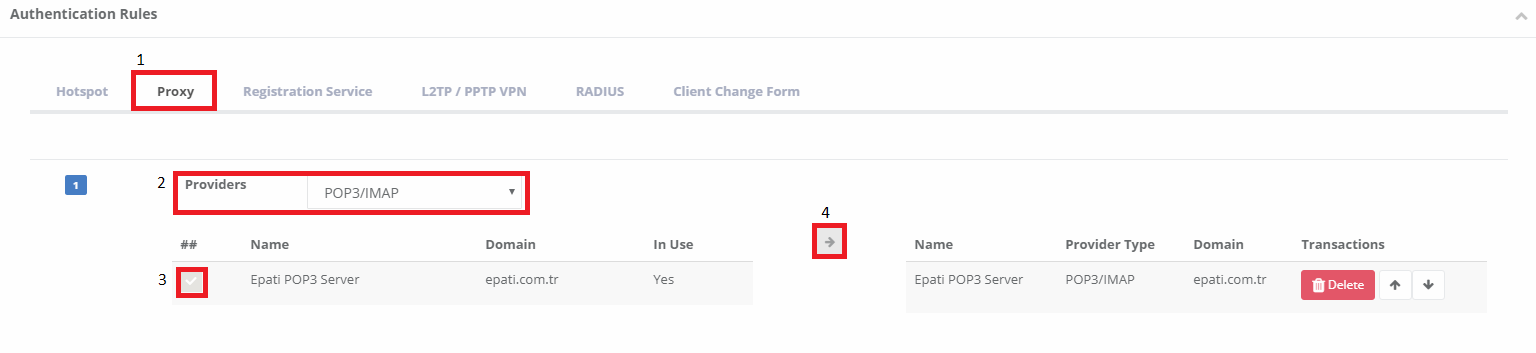
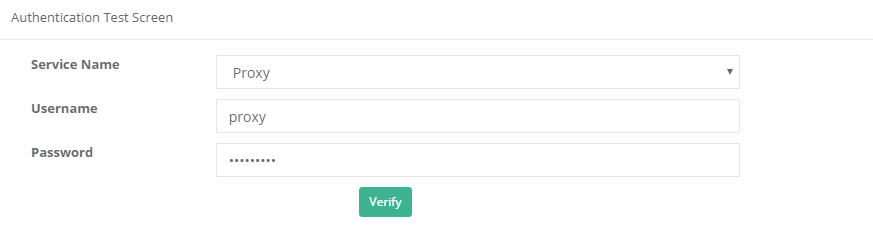
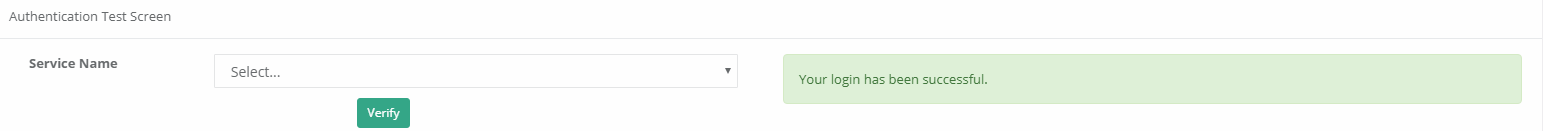
3) For testing, click to the Authentication Test page.
Since the for Proxy service has been assigned the Authentication method Proxy are selected. After entering the username and password registered on the server, the Verify button are clicked.
ePati Cyber Security Co.

Mersin Üniversitesi Çiftlikköy Kampüsü
Teknopark İdari Binası Kat:4 No: 411
Posta Kodu: 33343
Yenişehir / Mersin / TURKEY
Web: www.epati.com.tr
e-Mail: info@epati.com.tr
Tel: +90 324 361 02 33
Fax: +90 324 361 02 39