SSH Inspection
This is the section where SSH traffic passing through the Firewall is set to access options with different protocols.

Note: IP addresses are given as examples.
-
Only SSH servers connected with password auth can be set. (Public Key should not be.) `
-
A Shell connection must always be made for the server/client to be connected regardless of the options selected in the rules.`
-
After pressing the Add button, the operations are performed in the pop-up window.
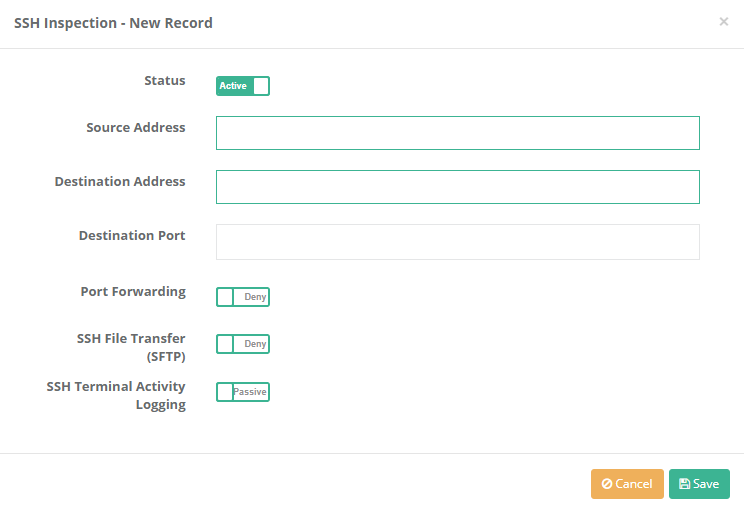
| FIELD | DESCRIPTION |
|---|---|
Status |
Active or passive status is selected. |
Source Address |
Enter the source address to which the rule will be applied. |
Destination Address |
Enter the destination address to which the rule will be applied. |
Destination Port |
The destination port(s) to which the rule will be applied are written. |
Port Forwarding |
Allow or Block options are selected for Port Forwarding. |
SSH File Transfer (SFTP) |
Allow or Block is selected for SSH File Transfer (SFTP). |
SSH Terminal Activity Logging |
Active is selected if SSH Terminal activity is to be logged. |
ePati Cyber Security Co.

Mersin Üniversitesi Çiftlikköy Kampüsü
Teknopark İdari Binası Kat:4 No: 411
Posta Kodu: 33343
Yenişehir / Mersin / TURKEY
Web: www.epati.com.tr
e-Mail: info@epati.com.tr
Tel: +90 324 361 02 33
Fax: +90 324 361 02 39

