SSH User Guideline
In order to log into Antikor as Administrator Putty program is used. We use Antikor’s internal IP in the event we access from inside the organization. Otherwise we use Antikor’s external IP if we access from outside the organization. Port number is 22022. The username is “admin” (Do not try port “22” from a remote site, as you will be blocked since it is added into Honeypot service. There will be no blocking if you add your IP address into ignored list.)
To open SSH control panel in AntiKor, a password is given by the company personnel or through “Console Panel”. Subsequent password operations can be performed with the administrator “ssh-password-change” command.
- adminConsole command
It is now possible to run the console to which we already have access via keyboard and monitor over SSH. When you execute “Logoff” command SSH console will be prompted again.
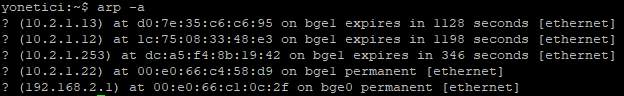
- arp command
IP is a protocol that allows us to learn the physical addresses of known devices. The command arp 172.29.148.5 gives us the MAC address of the device. The usage can be expanded by listing the parameters.
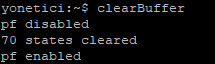
- clearBuffer command
clearBuffer command is the command to clear security rules connections. The below figure shows clearing of 38627 security rule connections.
- cd command
This command enables to navigate between directories. In order to go one path backwards use “cd.” command.
- clear command
It is the command of UNIX / Linux operating system. This clears the SSH screen that you are on.
- cluster-penalty-score command
Shows cluster penalty points.
- cluster-status command
Gives information about cluster status.
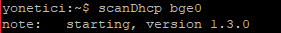
- scanDhcp command
This command scans the network environment for DHCP server.
The above image does not return any results because the DHCP server does not exist in the environment. Otherwise if the DHCP server existed, it would have notified us with a few output. Output results can be expanded by using other parameters.
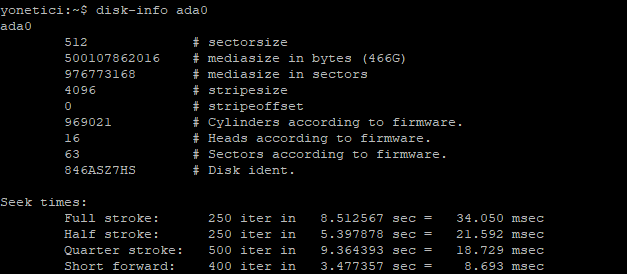
- disk-info command
This gives us disk performance information based on disk selection. The performance results of disk ada0 are as followes:
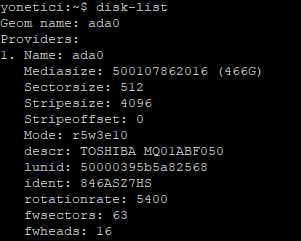
- disk-list command
This command shos information on existing disks. The following shows description, size and etc. details of disk ada0:
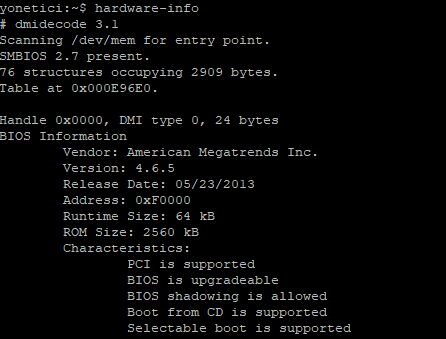
- hardware-info command
This command shows hardware details (e.g. RAM, CPU, etc.). You may see rest of the output by pressing Enter key.
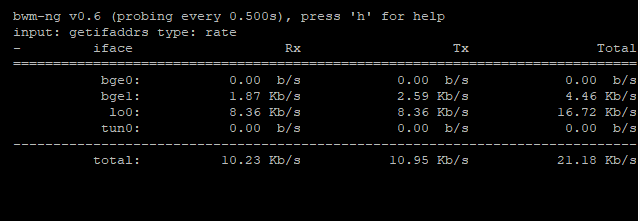
- interface command
When we type Ethernet and hit Enter real-tine send/receive traffic over all Ethernets and VLAN Ethernets will be showed. In this screen Rx Download, and Tx Upload. Press h to retrieve values and time information from the help menu. For example:
- d automatically converts values into Byte/KB/MB/GB.
- u shows values in bytes, bits, packets, errors. Every time we press u, it proceeds to the next one. In this screen packets number of packages per second, and errors number of errors per second.
- t current rate, max, sum since start, average for last 30s.
- a This shows unused ethernets.
- ”+” Default value is 0.500 s. Every time we press + time increases by 100 ms.
- ”-“ Default value 0.500 s. Every time we press - time decreases by 100 ms.
- n This changes input value.
- q This enables us to quit program.
The Ethernet program looks like the following:
- exit command
This is a command in UNIX/Linux operating system. This disconnects our SSH connection.
- grep command
This allows that the input files are used to perform a line-by-line search.
- help command
This opens help menu and has the same function as “?”.
- history command
This shows outputs of last commands used in SSH.
- http-logs command
This command shows instant http and http access requests.
-
ifconfig command
It is the command of UNIX / Linux operating system. The basic purpose is to assign IP to the vlan ethernet we have created with real ethernet, or to see the IP information by typing “ifconfig”. For example in order to assign an IP you may type the following:sudo ifconfig bge0 10.2.2.1/24 up -
iperf command
This is used to test network speed between two clients. IPerf -s parameter makes one client to act like a server. IPerf -c host parameter makes one client to act like a client.
- ipsecDebug command
This is used to show positive/negative outputs related to Ipsec VPN.
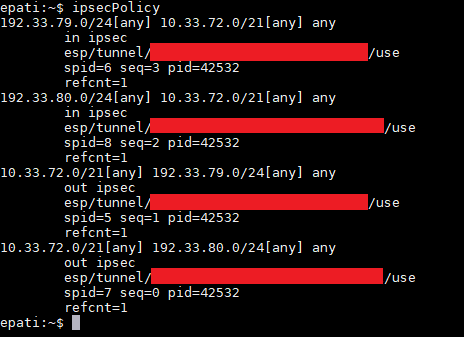
- ipsecPolicy command
This shows IPSEC VPN policies. IpsecPolicy output contains information on tunnels created.
(Note: Fields had to be highlighted with red, as external IP addresses were entered therein.)
- bandwidth-usage command
When we type user and hit Enter, this shows users of the firts Ethernet.
- kullanici –i bge0, This shows IPs on our Local Network and IP addresses on the Internet.
- kullanici –i bge1, It shows the actual IPs on the external side and the IP addresses on the internet.
- kullanici –i bge2, It shows IPs on server area and the IP addresses on the internet.
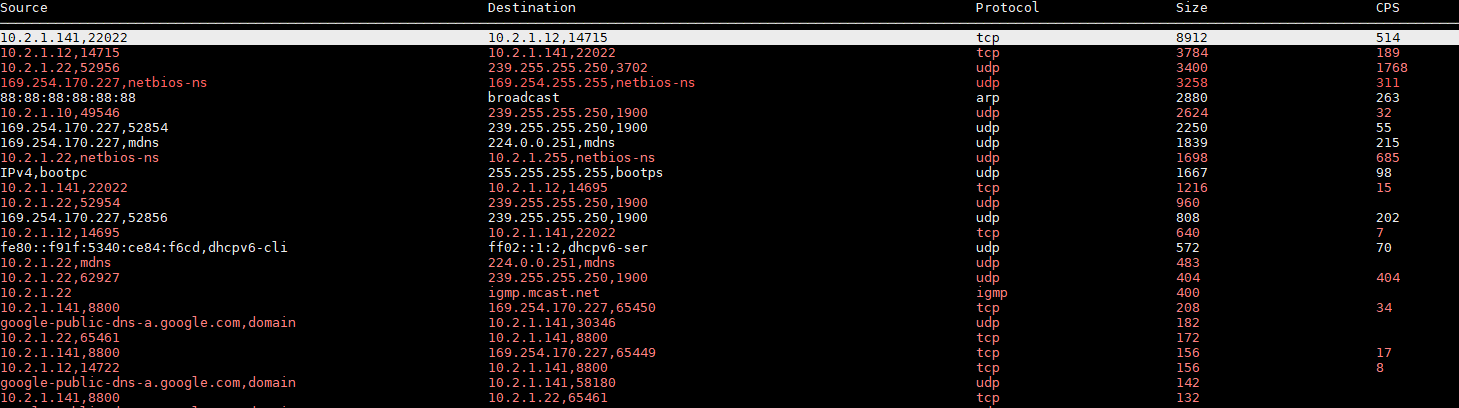
You can also see the 65536 port here while Instant Web Access shows only web requests in AntiKor’s web interface. So the torrent users reveal themselves. The below figure shows how an IP (10.2.1.22) downloads.
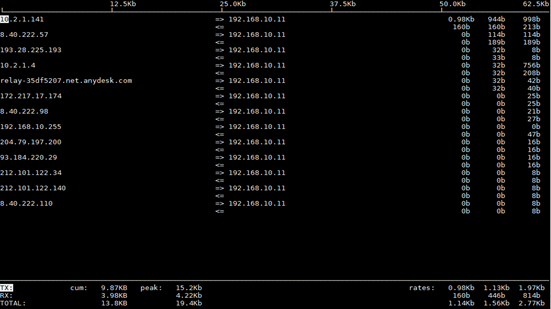
For example, if we are going to look up users only in one VLAN we need to type –i bge0.166.
- less command
We can see entire output, which is longer than the length of the screen by typing less command to fit it to size of the screen.
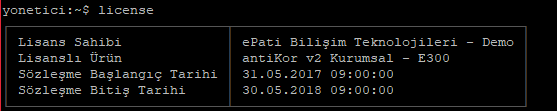
- license command
This shows license details of Antikor.
- lpath command
This lists authorized folders. In the image below, the authorized folders are listed.
- lsudo command
This lists the commands with sudo authorization. In the image below, the commands that can be used with sudo command are listed. We can use the following commands with sudo.
- more command
This is the command to be used to retrieve more details from a command. When I call for help menu for “less” command and add “more” command to it this will allow us to receive more detail on “less” command.
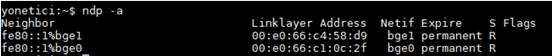
- ndp command
This has replaced such function as ARP, ICMP, etc. used in IPv4 protocol.
- ndp – a, Shows all relevant ndp entries.
- ndp –d, Parameter –d enables a super user to delete any entery for a hostname
- ndp –i, Coupled with paramater –s a ndp entry specified directory of interface to be used.
- ndp –I, This command deletes default Ethernet discovery interface.
- ndp –s → This creates a ndp entry for hardware address and hostname. The entry would be permanent unless command includes the term temp.
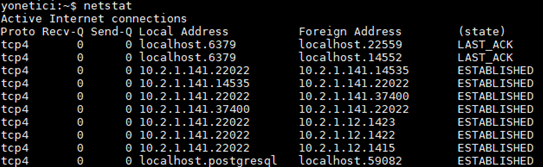
- netstat command
This is a command of UNIX/Linux operating system. This shows details of network connections (e.g. TCP, UDP, Port Number, Status, etc..) It has many parameters.
- For example: netstat –m, It gives us information on Network status.
- netstat –n, Shows list of connections made on the server.
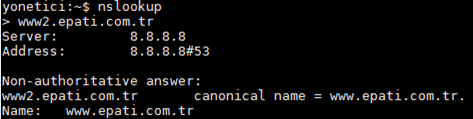
- nslookup command
This is used to check whether or not DNS server runs smoothly. The below figure shows result of inqury about Epati.
- package command
This provides details on version and status of Antikor packages.
- ping command
This is used to determine such functions of a target computer, server, and etc as operating status, distance, and etc. The following image shows ping perform on IP address 10.2.1.141 and successful response.
- Icmp_seq, Package header information will increase the header order in each ping packet.
- TTL (time to live), Time to live of package.
-
Time, Information about how long the Ping communication takes place..
- ping6 command
Ping6 is a model of Ping developed for IPv6 için geliştirilmiş modelidir. This is for those who use IPv6 protocol.
- radiusDebug command
This shows positive/nagative outputs in Radius server.
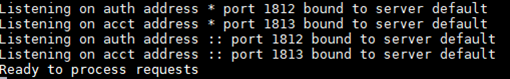
- radtest command
This has been developed to test Radius server.
- radtest –d This is a command to set up a Radius directory.
- radtest –t This is a command to specify IT check method.
- radtest –p This is a commond that enables us to select a protocol.
- radtest –x This is a command to parse error outputs.
- radtest -4 This is a command used to assign an IPv4 address for NAS.
-
radtest -6 This is a command used to assign an IPv6 address for NAS.
- route command
This is a command for UNIX/Linux operating system. It is use to clear or define a new route for the operating system.
- sudo route delete default → deletes the route then existed.
- sudo route add default 10.2.1.253
In the following image first of all the route was deleted and then it was re-added.
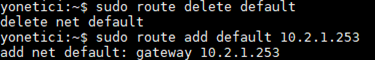
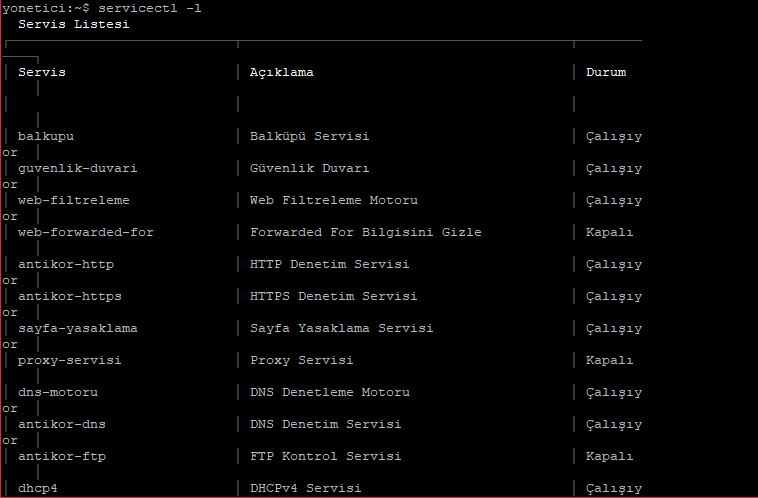
- servicectl command
It gives information about the status of the antiKor services. As shown in the following image, the services appear as “Running, Off, Bypass, or Not Configured”.
- ssh command
This is a protocol used for a remote conenction.
- change-ssh-password command
This is the command used to change SSH password (Note: Password characters are hidden and they are not visible when creating a password)
- sudo command
This enables commands, which are permitted to run with Sudo, to run with root permission. For example, when performing Route command or in the event we wish to delete a Route, which is already added, an error message will be displayed to us, as there is not any Sudo authorization.
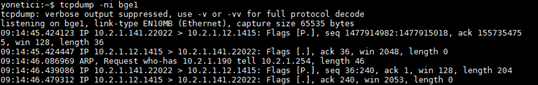
- tcpdump command
This is a command of UNIX/Linux operating system. It has many parameters. Examples of its usage are as follows:
tcpdump –D, This lists all interfaces which can be monitored over the network.
tcpdump –i bge0, This enables to monitor bge0 interface.
tcpdump -n src net 10.2.1.141, This command lists packages received from specified network address.
tcpdump –ni bge0, This command monitors local network traffic. It shows VLANs connected to this Ethernet over the VLAN.
tcpdump –ni bge0.166 host 10.2.2.2, This command shows traffic of only this IP on VLAN.
tcpdump ether host 11:22:33:44:55:66, This command shows traffic of computer with this MAC address.
tcpdump -i bge0.166 host 10.2.2.2 or 10.2.2.10, This command shows traffic of this 2 IPs.
tcpdump udp and (src port 161 or 162 or 514), This command shows UDP and those with source ports 161, 162, and 514. It is possible to give more example.
- telnet command
This is command used to connect to a remote computer or server. It is less secure than SSH. You can make a connection like the one in the following image, if the settings for telnet are configured, the connection session will be established.
- traceroute command
This command shows what routers the IP package passes through on the way to its target. traceroute command was run for Google’s DNS server. (Note: Fields had to be highlighted with red, as external IP addresses were entered therein.)
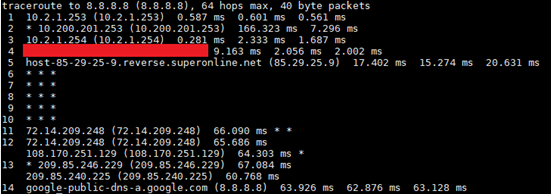
- traceroute6 command
This is the version of traceroute command developed for IPv6.
- trafshow command
This enables to monitor traffic by selecting Ethernet legs.
We first select the Ethernet leg to monitor:
We select Bge1 leg and proceed:
- apply command
This has the same function as the “Apply Changes” button in interface.
- apply –a, this command implements definitions pending to be implemented
- apply –cf, this command enables desired rule to be implemented.
- apply -fa, this command applies all definitions again.
For example, the following figure shows that we have re-implemented DNS settings.
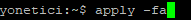
- uygula –fa, This command re-implements all commands in Antikor.
-
uygula –la, This command provides information on status of services.
- webBrowser command
This is the command to open all web services over the console. Epati Information Technologies’s web site at www2.epati.com.tr has been accessed over the console.
- reboot command
This command is used to restart Antikor from a remote site.
- ? command
This command prompts help menu and it has the same function as the “help”.
ePati Cyber Security Co.

Mersin Üniversitesi Çiftlikköy Kampüsü
Teknopark İdari Binası Kat:4 No: 411
Posta Kodu: 33343
Yenişehir / Mersin / TURKEY
Web: www.epati.com.tr
e-Mail: info@epati.com.tr
Tel: +90 324 361 02 33
Fax: +90 324 361 02 39