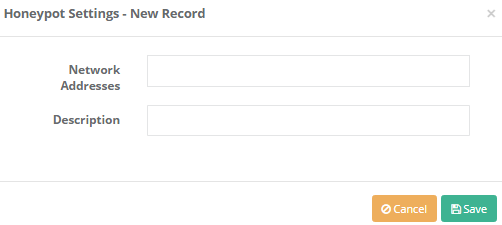
Honeypot Settings
They are traps set up to detect attacks against information systems. Although the services that it “appears to provide” on the matchine that it is installed varries depending on types of attacks that it attempts to get them into tramp, the basic logic of Honeypots is to lure intruders (automatized or manually induced) to networks where they are involved thereby raising awareness.
Since the machines that undertake this task do not offer any valid service, any traffic directed to them should be considered as suspicious and should be examined.
| FIELD | DESCRIPTION |
|---|---|
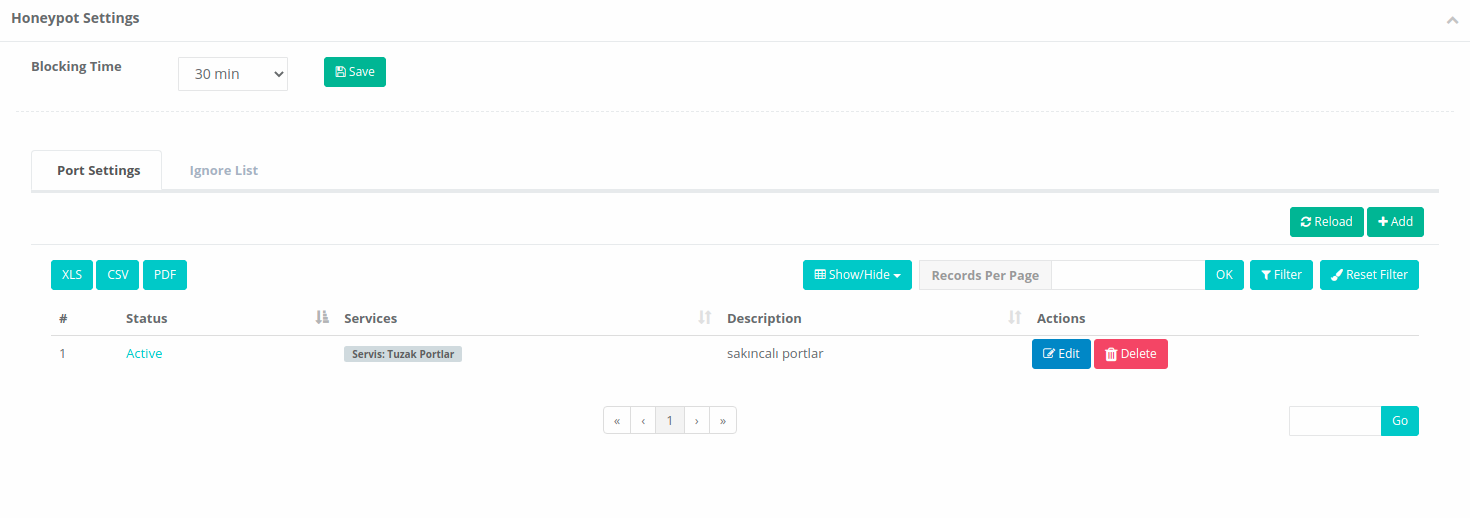
Prohibition Period |
Enter prohibition period. |
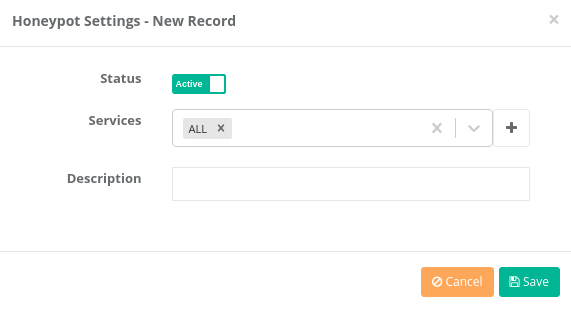
Honeypot Settings - New Record
| FIELD | DESCRIPTION |
|---|---|
Status |
Choose either active or passive as status. |
Services |
Enter services to be used for Honeypot. |
Description |
Enter description. |
Ignored
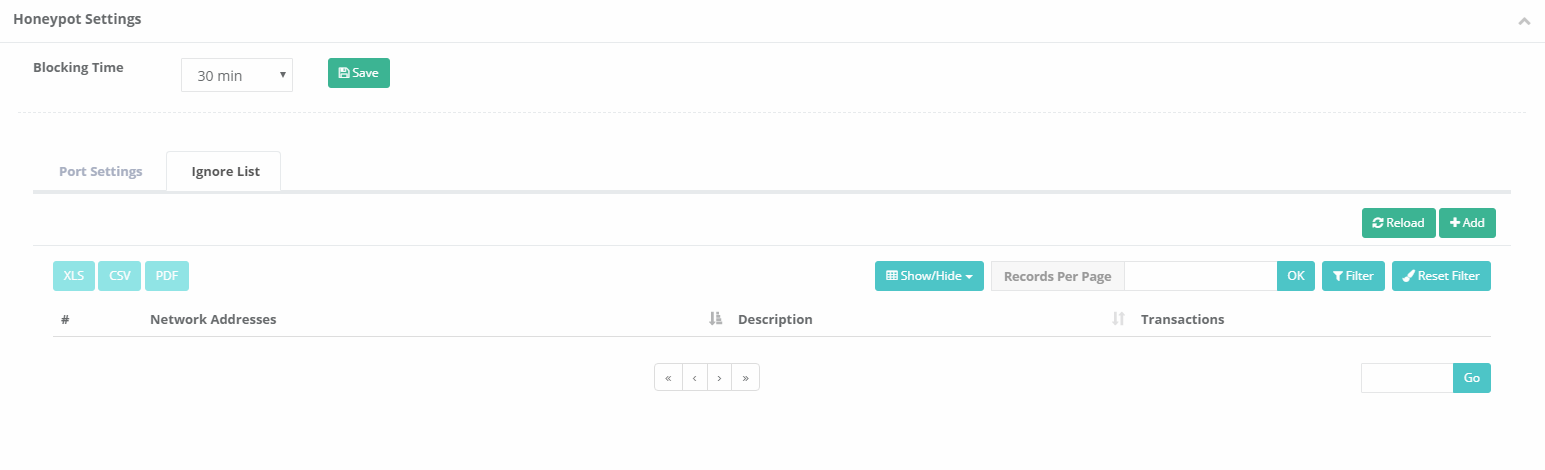
Ignored New Record
| FIELD | DESCRIPTION |
|---|---|
Network Addresses |
Enter network addresses that will not be blocked by Honeypot. |
Description |
Enter description. |
ePati Cyber Security Co.

Mersin Üniversitesi Çiftlikköy Kampüsü
Teknopark İdari Binası Kat:4 No: 411
Posta Kodu: 33343
Yenişehir / Mersin / TURKEY
Web: www.epati.com.tr
e-Mail: info@epati.com.tr
Tel: +90 324 361 02 33
Fax: +90 324 361 02 39