Security Rules
This is the part of the network that can allow or block the inside or outside of the network. Policies can be specified only based on source or destination address, or statefull can also be specified based on end-to-end traffic review method. Hits, Total Bytes and Active State can be examined for rules. Operations are performed in screen to be showed after Add buton is clicked on.
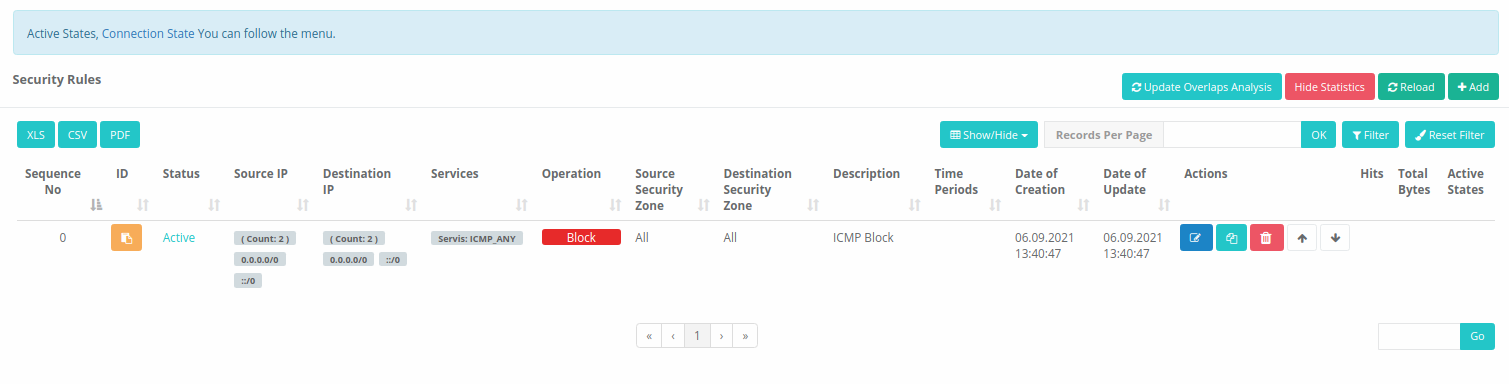
Hide Statistic
Hide information about hits, total bytes, and active states.
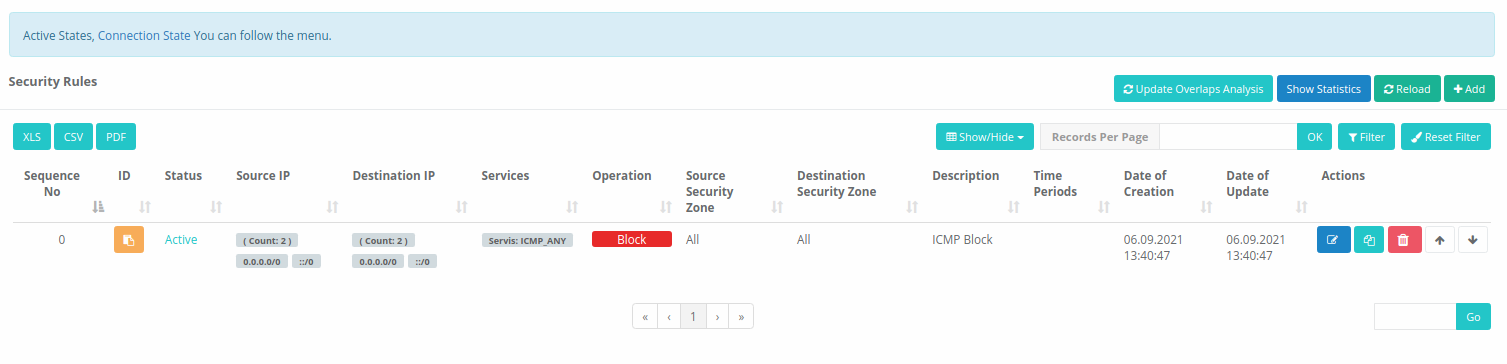
Show Statistic
Displays information about hits, total bytes, and active states.
Security Policies New Record
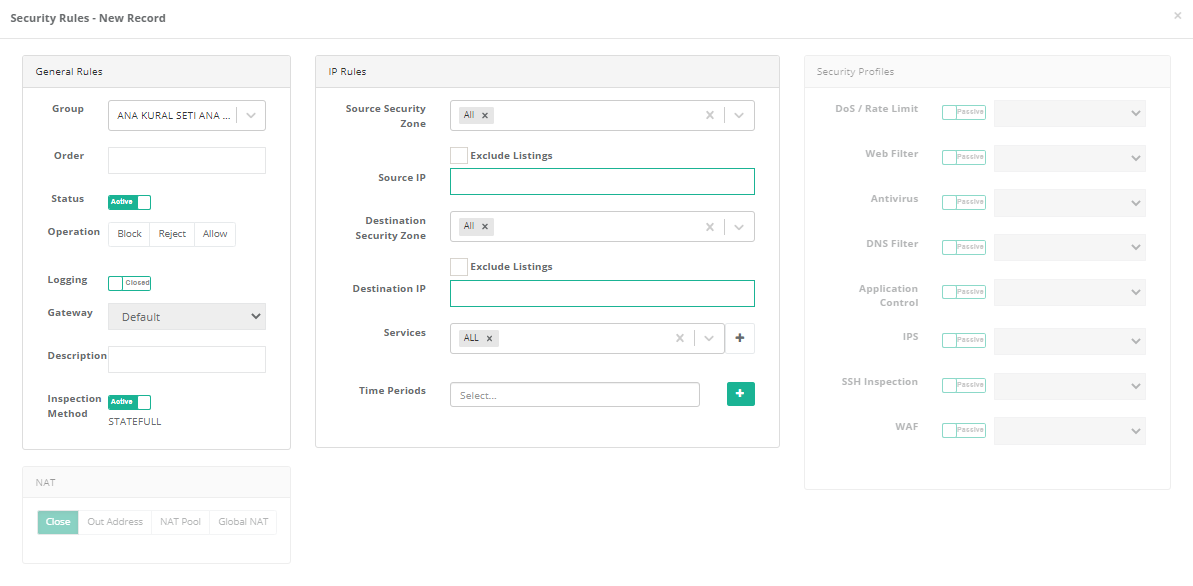
General Rules
| FIELD | DESCRIPTION |
|---|---|
Status |
Choose either active or passive as status. |
Operation |
Choose action type. |
Log Traffic |
By activating the button, Security rule logs can be sent to the Syslog server. |
Package Direction |
Choose direction to which the action is to be performed. |
Gateway |
The gateway is entered, if there is only a default, the user is not selected. |
Description |
Enter description. |
Inspection Method |
Choose inspection method. (Statefull or Stateless) |
IP Rules
| FIELD | DESCRIPTION |
|---|---|
Source Security Zone |
Select the source security zone to which the security rule applies. |
Source IP |
Enter The source address which will be applied the rule. If the option Exclude Listeners is selected, the IP addresses except the IP address entered in Source address will be processed. |
Destination Security Zone |
Select the destination security zone to which the security rule applies. |
Destination IP |
Enter The source address which will be applied the rule. If the option Exclude Listeners is selected, the IP addresses except the IP address entered in destination address will be processed. |
Services |
Select the defined service or services to which the rule applies. |
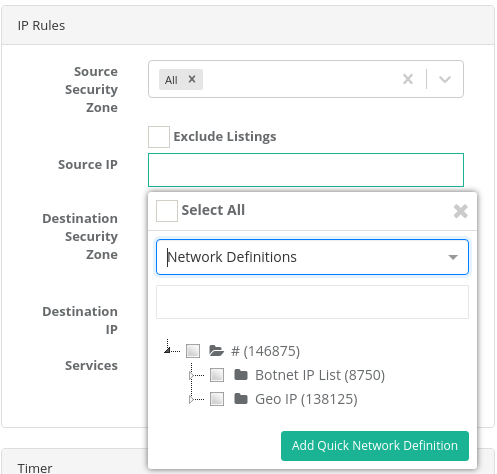
Network |
Choose one of the networks assigned before which affect by the rule. |
Note: If network definitions are used in security rules, a network definition can be added using the Add Quick Network Definition button without going to the corresponding menu and can be used in Security Rules.
Timer
| FIELD | DESCRIPTION |
|---|---|
Time Periods |
Specified time & date range, the times when the security rule will work are determined. |
Security Profiles
| ALAN | AÇIKLAMA |
|---|---|
DoS / Connection Limitation |
By activating the button, selection can be made. |
Web Filtering |
By activating the button, selection can be made. |
Antivirus |
By activating the button, selection can be made.. |
DNS Filtering |
By activating the button, selection can be made. |
Application Control |
By activating the button, selection can be made. |
IPS |
By activating the button, selection can be made. |
SSH Check |
By activating the button, selection can be made. |
WAF |
By activating the button, selection can be made. |
NAT
It has a single line NAT feature.
ePati Cyber Security Co.

Mersin Üniversitesi Çiftlikköy Kampüsü
Teknopark İdari Binası Kat:4 No: 411
Posta Kodu: 33343
Yenişehir / Mersin / TURKEY
Web: www.epati.com.tr
e-Mail: info@epati.com.tr
Tel: +90 324 361 02 33
Fax: +90 324 361 02 39

