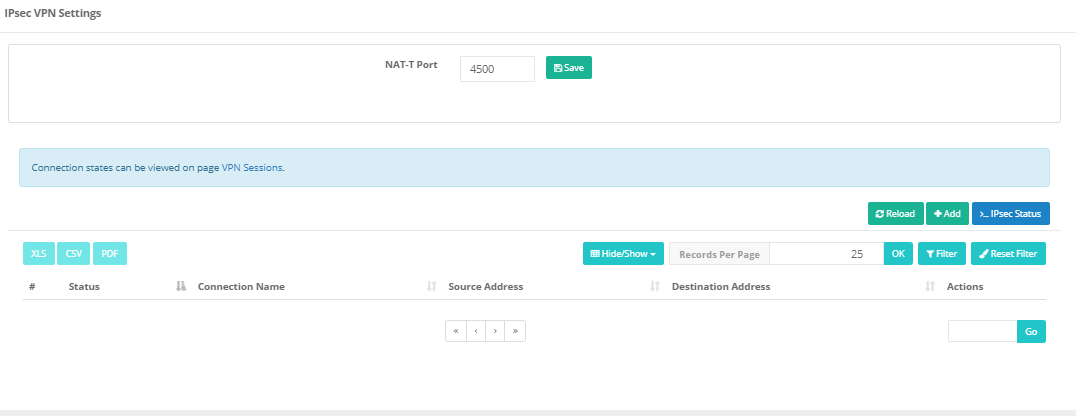
IPsec VPN Settings
The AntiKor IPSec VPN module can operate in either IPsec Transport or IPsec Tunnel mode. The Phase1 and Phase2 settings of the created IPsec connection can be easily configured in a single screen, lists of access-authorized IP addresses, and the protocol to be used during transmission can be configured with a user-friendly interface.
NAT lama support is available on the IPsec interface. In addition, created records can be copied.
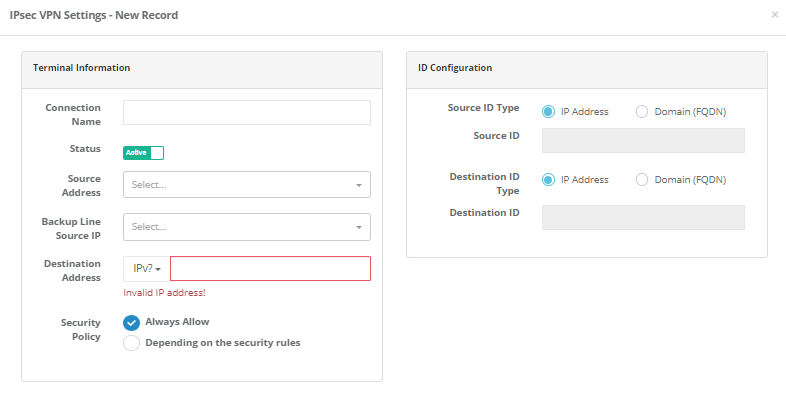
IPsec VPN Settings New Record
Note: When clicking on the access section of IPSEC VPN settings, the access list comes.
Note : When you click on the Accesses section in the IPsec VPN Settings, the Access list appears.
IPsec VPN Accesses List
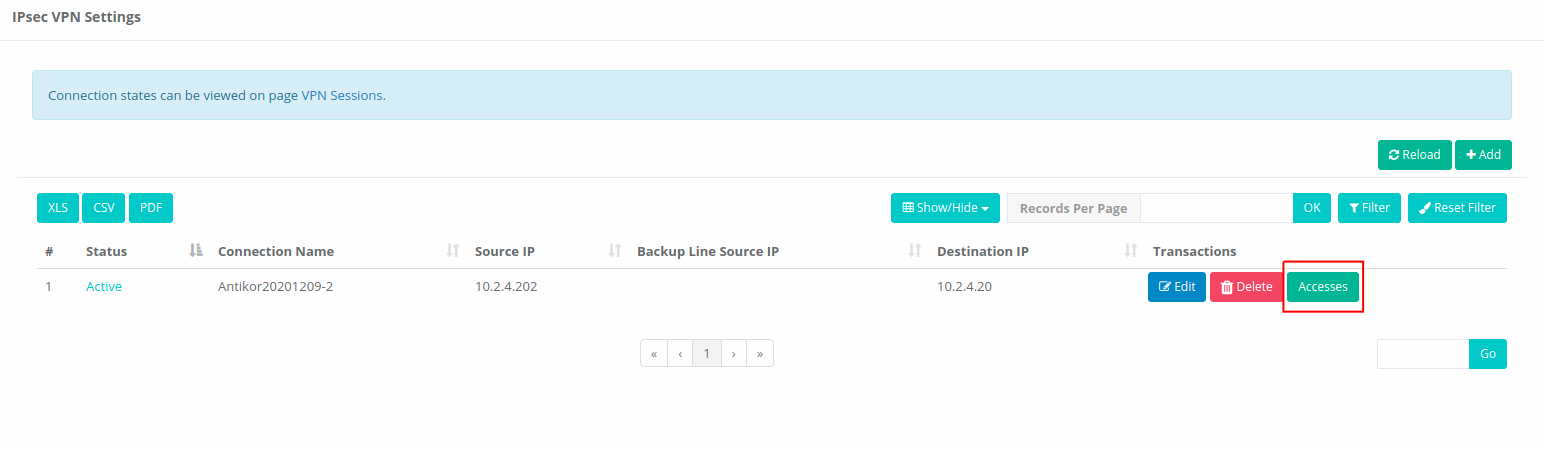
Click on the Accesses screen below. This screen controls IPsec VPN access.
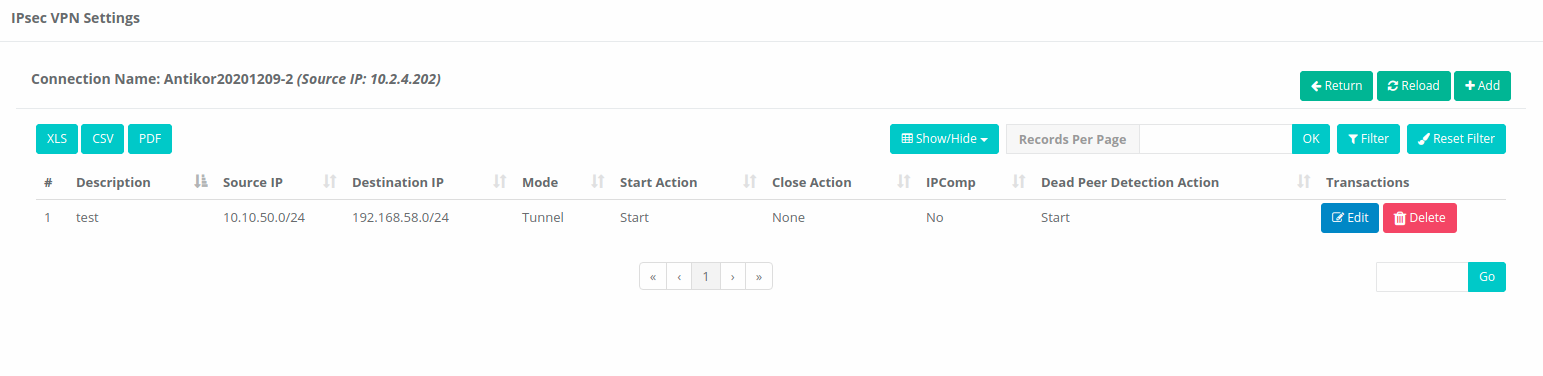
IPsec VPN ACL New Record
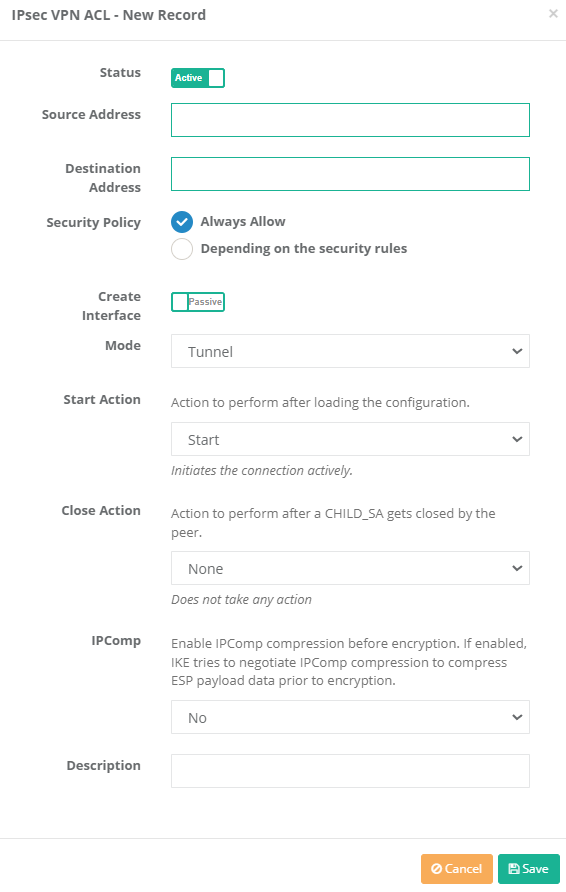
IPsec VPN ACL Edit Record
| FIELD | DESCRIPTION |
|---|---|
Situation |
Active or passive is selected. |
Source Address |
Source IP address, IP range, network definitions and network interfaces are selected by selecting. |
Target address |
The target IP address, IP range, network definitions and network interfaces are selected by selecting. |
Security policy |
Security policy is selected. |
Mod |
The transfer (Transport) is selected from one of the tunnel or external mode. |
Explanation |
Description is written for the access list record. |
END INFORMATION
| FIELD | DESCRIPTION |
|---|---|
Connection name |
The connection name is written. |
Situation |
Active or passive is selected. |
Source Address |
The source address is selected. |
Spare line welding IP |
Selected IP welding IP. |
Target address |
One of the IPV4 or IPV6 address family is selected and the target IP address is written. |
Point-to-Point Configuration
FIELD|DESCRIPTION
—–|—–
Create Interface|Interface/interface creation is selected as active or passive.
Security Zone|The security zone is assigned.
Source IP|The source IP is assigned.
Opposite IP|The opposite IP is assigned.
ID Configuration
| FIELD | DESCRIPTION |
|---|---|
Source ID Type |
Choose source ID type. |
Source ID |
Enter source ID. |
Target ID Type |
Choose target ID type. |
Target ID |
Enter target ID. |
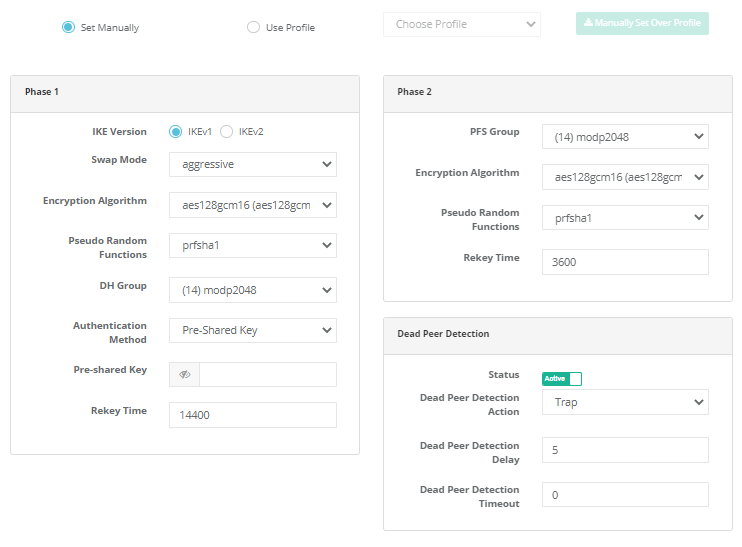
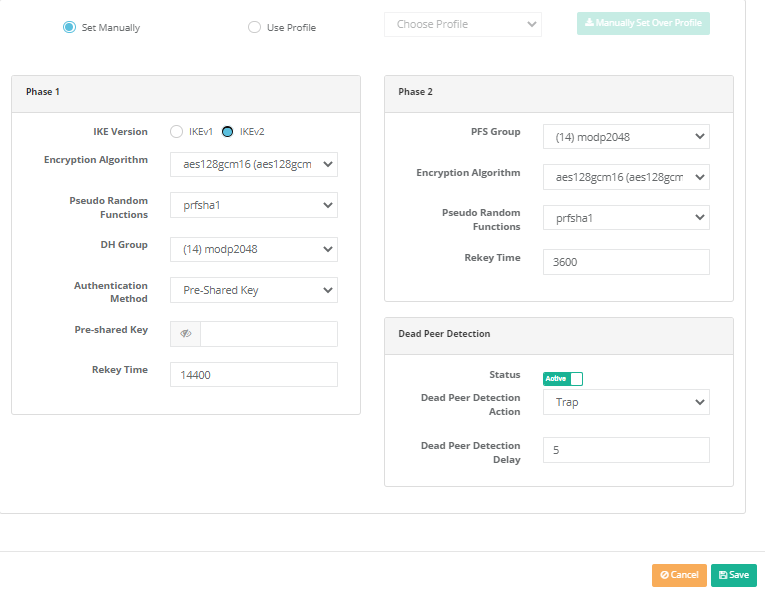
Profiles
| Field | Description |
|---|---|
Set Manually |
It is used for manual adjustment of Phase 1 and Phase 2 settings. |
Use Profile |
It is used to adjust the phase 1 and phase 2 settings with the help of profile. |
Choose Profile |
If Use Profile is selected, the previously ready profile must be selected. |
Manually Set Over Profile |
It is used to manually set the selected profile. |
Phase 1
| FIELD | DESCRIPTION |
|---|---|
IKE Version |
Select Internet Key Exchange version. |
Swap Mode |
Choose swap mode. |
Encryption Algorithm |
Choose encryption algorithm to be used. |
Hash Algorithm |
Choose hash algorithm to be used. |
DH Group |
Choose DH group. |
Authentication Method |
Choose authentication method. |
Pre-shared Key |
Enter pre-shared key. (Authentication method if Pre-Shared Key is selected) |
Certificate |
Choose Certificate. (Authentication method if Certificate is selected) |
Peer Certificate |
Choose Peer Certificate.(Authentication method if Certificate is selected) |
Phase 2
| FIELD | DESCRIPTION |
|---|---|
PFS Group |
Choose PFS group. |
Encryption Algorithm |
Choose encryption algorithm to be used. |
Authentication Algorithm |
Choose authentication algorithm to be used. |
Compression Algorithm |
Choose compression algorithm. |
Dead Link Detection
| FIELD | DESCRIPTION |
|---|---|
Dead Link Detection Behavior |
The action to be taken on the dead link detection timeout is selected. When Close (Clear) is selected, it closes the connection and takes no further action. |
Dead Link Detection Time |
The time it takes to reconnect when the IPSec connection is lost. |
Dead Link Detection Timeout |
If timeout 0 is selected, dead link behavior will be repeated during dead link detection. If a timeout is entered, dead link detection will not be performed when the timeout expires. |
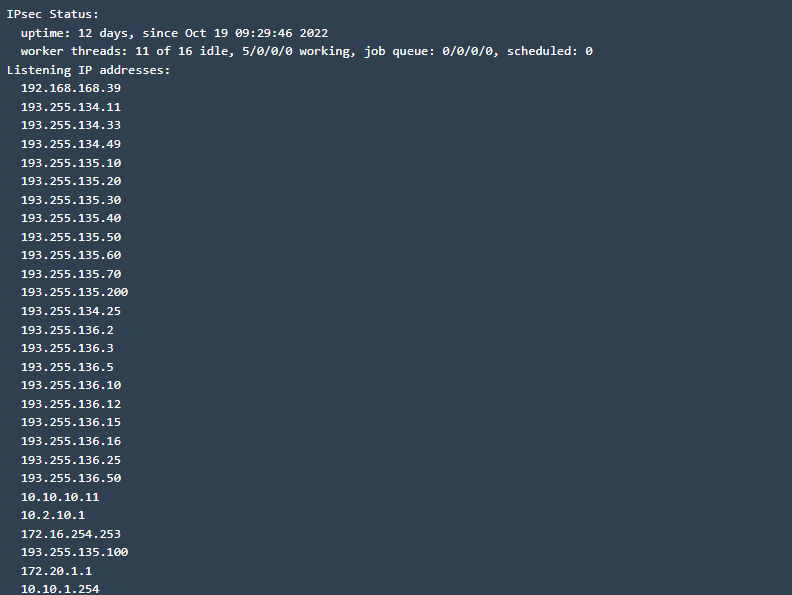
There is an IPsec status window.
IPSec Status
ePati Cyber Security Co.

Mersin Üniversitesi Çiftlikköy Kampüsü
Teknopark İdari Binası Kat:4 No: 411
Posta Kodu: 33343
Yenişehir / Mersin / TURKEY
Web: www.epati.com.tr
e-Mail: info@epati.com.tr
Tel: +90 324 361 02 33
Fax: +90 324 361 02 39

